Private Video Phishing: The Newest Threat to YouTube Creators
Creators are being hit with a slick scam that starts with a real-looking YouTube email and ends with malware on your computer. Below is a plain-English breakdown of how it works, why it fools smart people, and what to do about it—plus a short technical appendix and references.
The playbook in 5 steps


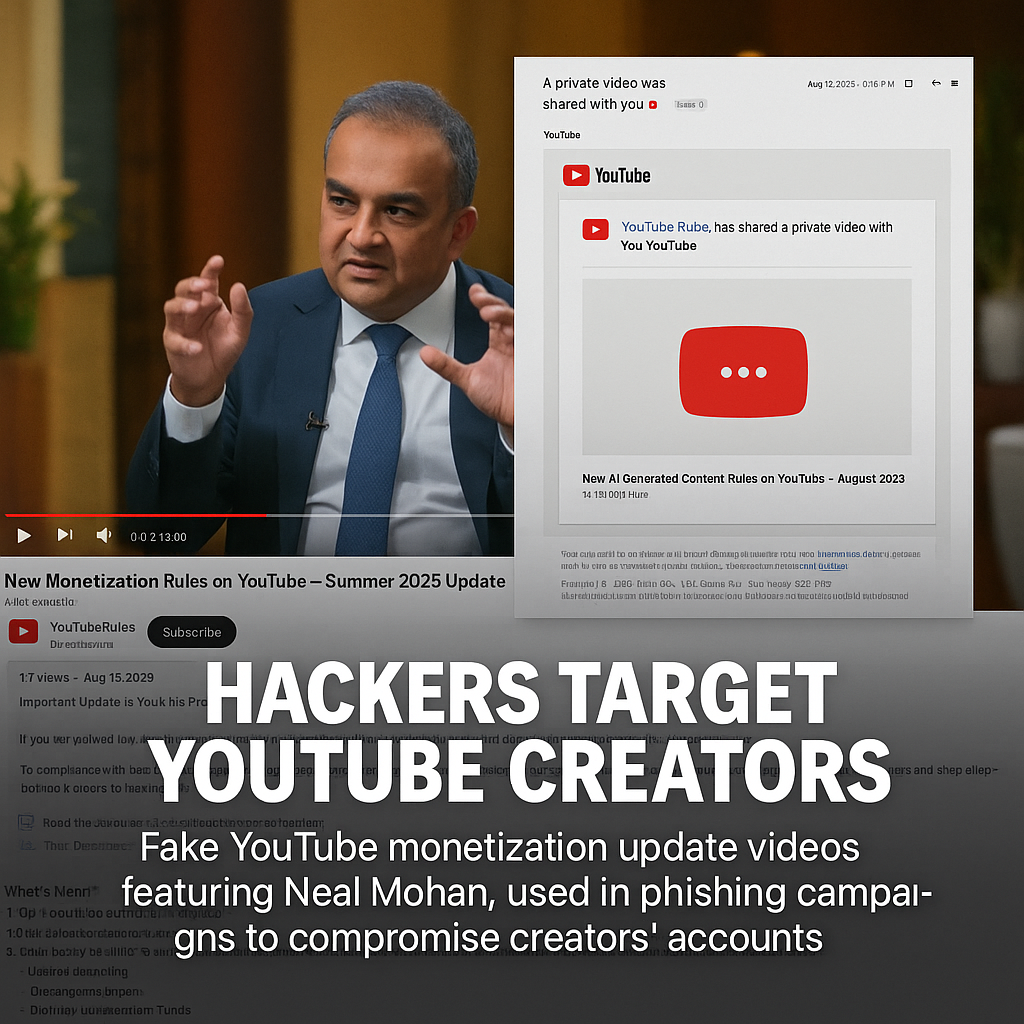
- Trust hook: You get an email titled “A private video was shared with you.” It often passes SPF/DKIM/DMARC because the attacker actually uses a real YouTube channel to share a private or unlisted video. That makes the notification itself legitimate. YouTube has warned creators that any private video “from YouTube” is a phishing scam—don’t follow the links. Google Help+1
- Authority theater: The private video pretends to be from policy, “YouTube Rules,” or even shows a (deepfake) clip of YouTube’s CEO with urgent claims about Partner Program/monetization updates. Independent reporting confirms this deepfake-style angle has been used to pressure creators. BleepingComputerThe Verge
- The off-platform pivot: The video description pushes a shortened link to a “document” or “update.” The link lands on a download—commonly an MSI installer posing as “YouTube Studio update” or “Monetization policy.” YouTube’s policy is clear: content that tricks people off-platform is not allowed; report it when you see it. Google Help
- Execution on your machine: Running that “update” installs a small program that drops extra files into hidden or system folders and may wait quietly (to evade sandboxes) before trying to steal your browser sessions, tokens, or passwords—especially anything that can log into Google/YouTube.
- Account takeover: With a valid session cookie, the attacker can change recovery options, add managers, push scam videos/livestreams, or redirect monetization. If you use the same browser profile for email, banking, crypto extensions, etc., exposure can go beyond YouTube.
Why this works
- Headers ≠ safety. People are trained to check SPF/DKIM/DMARC—these do pass, because the platform email is real. The scam lives in the video description and external download, not in a forged sender line. Google Help
- Urgency + exclusivity. “7-day deadline,” “policy changes,” “your monetization is at risk” push you to install now. Scammers know creators fear losing the channel. The Verge
- Deepfakes as accelerant. A CEO-looking video reduces skepticism just enough to get the click. BleepingComputer
What to do (practical, fast)
- Don’t open “updates” from videos or short links. YouTube will not push software via a private video. If in doubt, go to Studio directly in your browser—not via links. Google Help
- If you clicked/downloaded:
- Disconnect from the internet.
- On a separate, clean device, change your Google password and log out of all sessions; review devices and revoke suspicious OAuth access. Google Help
- Run a reputable AV/EDR scan or ask IT to reimage if you handle sensitive accounts.
- Report the channel/video from the email or the video page—YouTube explicitly asks creators to report these. Google Help
Short technical appendix (for teams)
- One known sample delivered by this campaign (MSI named like “YouTubeStudio 2025 Update For Creators.msi”) is flagged on VirusTotal; you can verify detections and share the SHA-256 with your SOC:
646f485e0b4c37f9754857a9abe61138eb3500081929c42628de980b6e2e9264. VirusTotal - Typical behavior: drops a launcher and DLLs under
%ProgramData%/%AppData%, uses DLL search-order hijacking, delays network beacons, and targets browser data/sessions to enable account takeover. Public reporting ties similar loader techniques to credential-theft toolchains. (Attribution names vary—focus on behaviors, not the family label.) harfanglab.ioInfosecurity Magazine
How to harden a creator workflow (reasonable, not overkill)
- Policy: treat all “policy changes” as in-product only; anything via video/shortlink is suspect. Cross-check in YouTube Studio or official Help threads. Google Help
- Downloads: block
.msifrom URL shorteners at the gateway; prefer browser isolation for creator accounts. - Access hygiene: dedicated browser profile for YouTube; hardware key (FIDO2) on your Google account; least-privilege roles for managers.
- Awareness: show your team YouTube’s own advisory so this isn’t just “another security email.” Google Help
Bottom line
The scam abuses real YouTube notifications and a private video to smuggle a malicious download past your gut checks. The right response isn’t to panic about email headers; it’s to never install software or open “documents” from video descriptions, to verify claims inside YouTube Studio, and to lock down accounts if you’ve interacted with one of these lures. YouTube has publicly confirmed this exact tactic; treat it as hostile by default. Google Help+1The Verge
References
- YouTube community advisory on phishing via private video sharing (official). Google Help+1
- VirusTotal record for a representative MSI used in this campaign (hash shown above). VirusTotal
- Coverage of AI-generated CEO video used in this lure. BleepingComputerThe Verge
- YouTube Spam & deceptive practices policy and account security guidance. Google Help+1
Detections & hunts
1) EDR/SIEM hunts (Windows)
- Path creation:
%ProgramData%\fevalid\*or%AppData%\fevalid\*. - Process chain:
msiexec.exe→ write/execute new EXE in ProgramData → DLL loads from same dir. - File names:
Cu-Shad.exe,Chime.exe,zcl.dll,Zxl.dll,zpsres.US.dll. - Network policy: block
.msidownloads from URL shorteners; alert on user-initiated MSI executions sourced from HTTP(S).
2) YARA (rough heuristic)
yaraCopyEditrule YouTube_MSI_Fevalid_CuShad_Jul2025
{
meta:
desc = "Detects fevalid/Cu-Shad/ZPS17 loader drops"
author = "IR"
date = "2025-08-13"
strings:
$s1 = "fevalid\\Cu-Shad.exe" ascii nocase
$s2 = "ZPS17 Media Server" ascii
$s3 = "AppliedInformatics_UPnP/1.0" ascii
$s4 = "Poco/ActiveMethod.h" ascii
$s5 = "Monetization" ascii
condition:
uint16(0) == 0x5A4D and 2 of ($s*)
}3) Sigma (process creation; simplify per your schema)
yamlCopyEdittitle: MSI Drops Cu-Shad.exe into ProgramData\fevalid
logsource: { category: process_creation, product: windows }
detection:
sel1:
Image|endswith: '\msiexec.exe'
sel2:
CommandLine|contains: '.msi'
sel3:
TargetFilename|contains|all:
- '\ProgramData\fevalid\'
- '.exe'
condition: sel1 and sel2 and sel3
level: highIOCs (consolidated)
Delivery
MonetizationInfo.short[.]gy(shortlink host used in lure)
Parent payload
YouTubeStudio 2025 Update For Creators.msi— SHA-256646f485e0b4c37f9754857a9abe61138eb3500081929c42628de980b6e2e9264
Dropped / executed
%ProgramData%\fevalid\Cu-Shad.exe—77c80390362223142f159c6b8b43598f4431517488b9c8e99dd0d591e85419a8%ProgramData%\fevalid\zcl.dll—621cf7b94118cbc9fda627a037b4eedac558987050669c128065579ea18cbeed%ProgramData%\fevalid\Zxl.dll—11da5ff336f1ca4213296308d106862326398fdf1d191f9b08927996cf876667%AppData%\fevalid\Chime.exe—adb8347dfa1b1df1ca2211fe4d7e82f27ced939f1bf3d52548e52bc9e23fc52c- Additional DLLs (MSVC/IPP/libiomp5md/zpsres) — hashes in your HA output.
Not C2: 62.60.226.104:4433 observed in ANY.RUN belongs to the sandbox agent process; ignore for blocking.